We have the technology and infrastructure to keep your website online even while under the severest of DDoS attacks. You don't need to make any additional software or hardware investments. The protection can be activated in minutes - right after your order, and you will be able to forget about the DDoS threat forever. Our mitigation technology is truly hassle-free, just make an account, give us some information about your hosting structure and we will take care of everything else.
Your business can be cost-effectively protected from all types of DDoS attacks without exception. Guaranteed: we are so confident in the power and effectiveness of our service that we are the only company in this business offering 100% money back guarantee if you're not satisfied with us. And now, with free setup for all levels of protection, and a free 24-hour test across all packages, you can rest assured your business will be well protected from any DDoS attack.
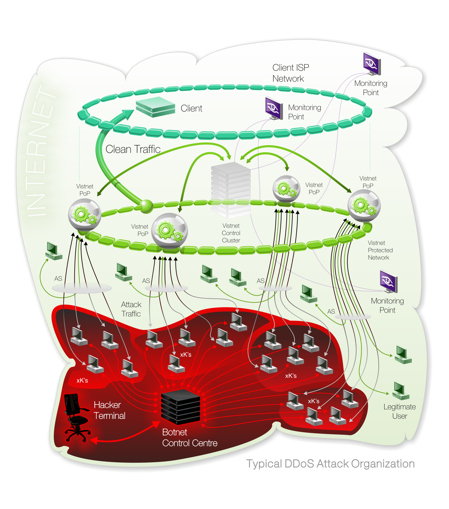
On the diagram left (click image for full size) you can see a typical DDoS Attack organization. Hacker(s) sit at a remote terminal connected to a Botnet Control Centre, which in turn commands individual user machines, collectively called Botnet. These machines are compromised prior to the attack with special software that allows the hacker to exploit them.
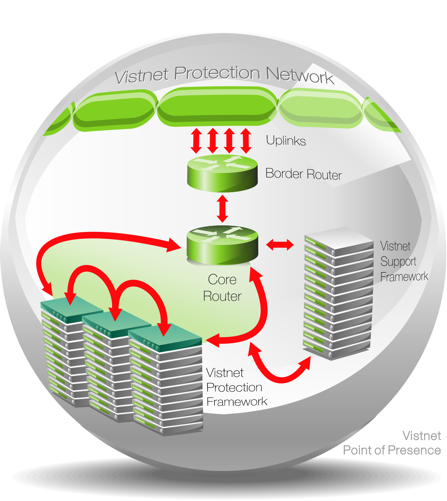
Subscribing to our service, you are protected from DDoS attacks, due to the fact that Bad/Attack traffic is directed to our protected network. It consists of a number of Points of Presence (PoP) that we have around the world to ensure better connectivity with your visitors, allowing us to receive and balance malicious traffic globally. See diagram below for schematics of one of our PoP's.
When bad traffic reaches one of our PoP's it is being filtered and cleaned, then sent out to you as Clean traffic. Thus, your site's accessibility is ensured throughout the duration of any type of DDoS Attack.
To ensure proper and effective functioning of the filtering and cleaning processes in our PoP's, we have a Control Cluster, which monitors the work of the PoP's, analyses the issues and sends fresh and revised instructions as necessary. In addition, we have Monitoring Points scattered throughout the globe, that report your site's status from real visitor locations. These also send information to the Control Cluster, thus effecting corrective action.
Our solution works like a proxy in front of your site, takes over your traffic, filters it and sends you back only good clean traffic. Here's what needs to happen:
- Upon placing an order you provide us with your domain name, backend IP address and SSL certificate with SSL private key (if any)
- We create a DDoS protection service account for you, and send your Protected IP address and all other settings almost immediately after signup for our service
- You change your domain's DNS records so that it is directed to our Protected IP address
- You make your backend accessible* to our protected network
- Your site's traffic is now redirected through our protected network
From then on, our service filters and cleans your traffic from DDoS Attack traffic.
- Our service sends the client requests to your backend server and serves the client back with the requested information. Real user IP addresses are sent with X-Forwarded-For header
- DDoS Attack traffic is rejected on our network
It is best to block all traffic on your firewall, allowing only our network. Balancing the traffic between multiple IP addresses and restricting it to exclude specific countries enhances mitigation results
* If your backend is already under attack it may not be possible for us to access it. In this case you can either request a fresh dedicated IP from your hosting company or close port 80 and open another one for us.